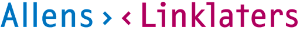Secure, anonymous reporting to empower your organisation
Ensure workplace safety, integrity and compliance. Tackle misconduct, enhance employee engagement and maintain business standards.
Australia's leading solution for workplace integrity and compliance
Designed to align with Australia's unique legal framework, Elker facilitates greater employee engagement, proactive issue detection, and secure whistleblowing. We support businesses in navigating the complexities of the Sex Discrimination Act, Fair Work Act, and other key regulations, ensuring they are prepared to handle workplace incidents like bullying, sexual harassment, and financial misconduct.
See all features →Compliance expertise
Meet compliance with the Sex Discrimination Act, Corporations Act, Fair Work Act, and more, ensuring full legal compliance in Australia.
Boost employee engagement
Foster a culture of open communication, allowing employees to speak up and be heard.
Early detection of issues
Detect and address workplace concerns early, averting potential litigation and reputational damage.
Robust whistleblowing mechanisms
Enable secure disclosures for financial crimes and safety violations, protecting whistleblowers.
Anonymous reporting of workplace issues
Report bullying, harassment, and pay discrepancies without fear of victimisation.
Effective incident management
Comprehensive reporting pathways and incident management for resolving workplace incidents efficiently.
Data-driven insights
Leverage real-time data to understand and improve your organisational dynamics.
Uncompromised data security
With ISO27001 standards, ensure all sensitive information is handled with utmost security.
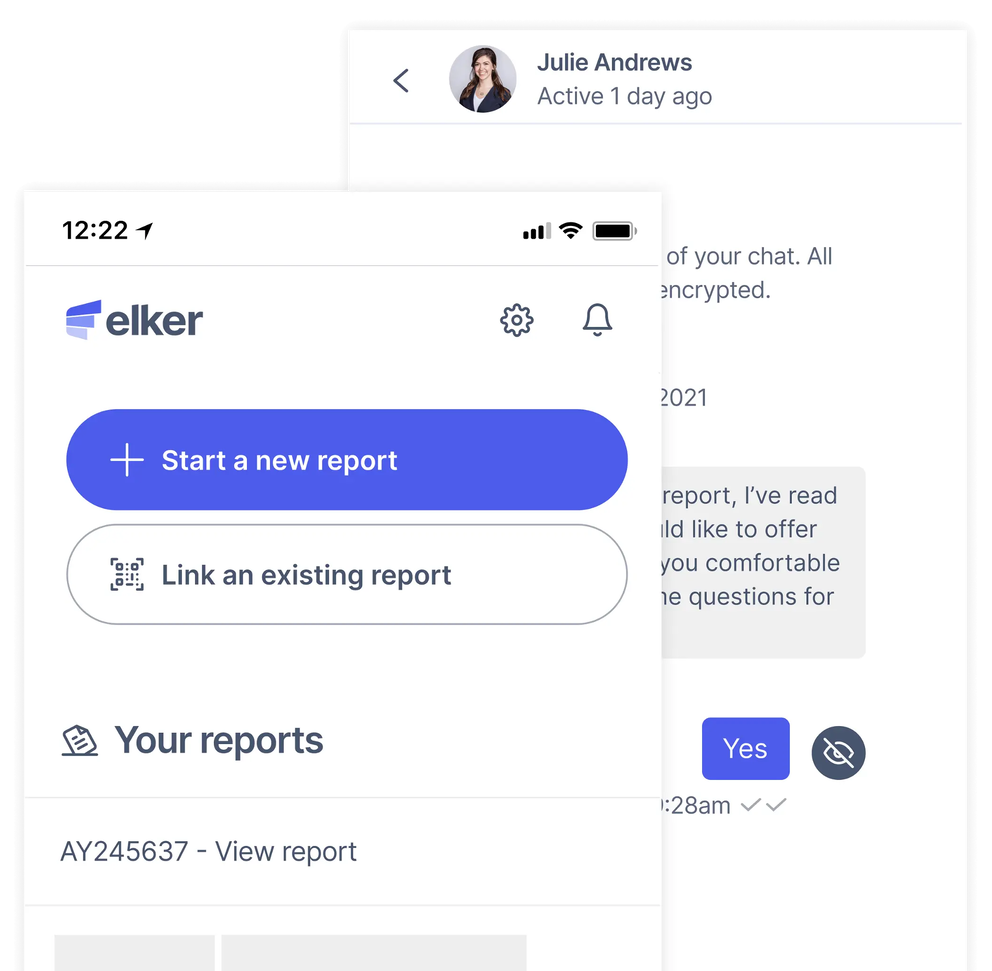
Comprehensive reporting tools for feedback, support, early intervention, and whistleblowing
Elker offers a secure channel to capture disclosures, identify whether whistleblower protections apply and manage the case through its lifecycle.

Early intervention with anonymous reporting
Elker’s allow your employees to reach out and share what's on their minds. Address suggestions and minor concerns through to serious misconduct in the workplace. Elker allows you to resolve issues quickly and improve employee happiness and company culture.

Privacy and anonymity
Users can choose to remain anonymous or for reports to remain confidential. They can nominate a colleague to report with, upload evidence, and chat through a secure 2-way message service. Elker guides all parties through the process to ensure privacy and safety.

Comprehensive triage options
Users nominate the reporting pathway and responder. They can track the progress of their case, decide on outcomes and get alerted to similar issues. Workflows are flexible and customisable for your organisation’s needs.

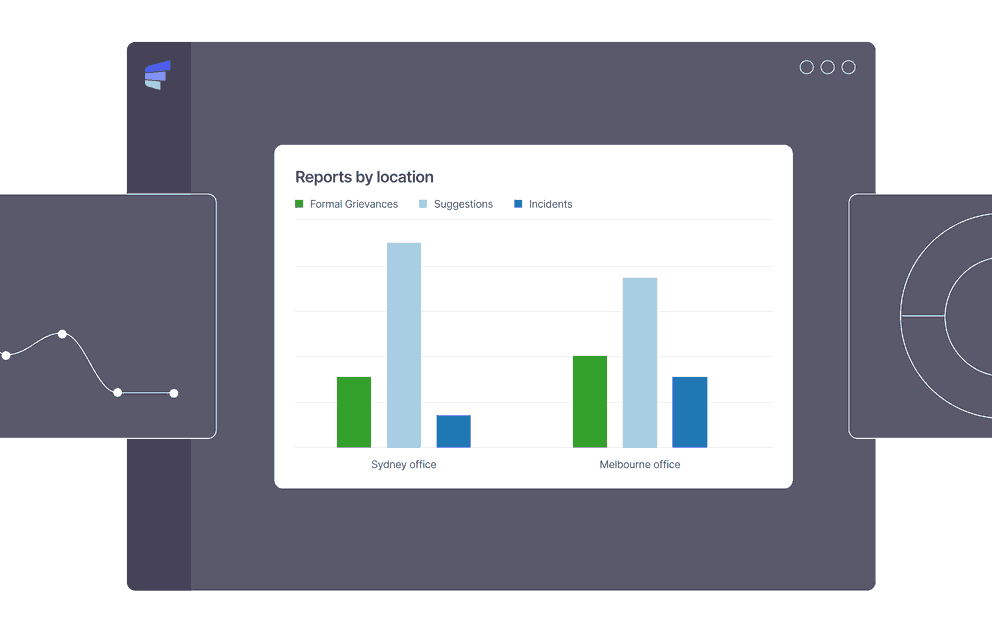
Meet targets with real-time data and analytics
With Elker’s analytics and real-time reporting dashboard, you can view trends in your company culture and set organisational targets. Foster a speak-up culture where employees, students and members feel safe.
From setup to success
We understand that introducing new tools can often mean organisational changes. This can be a significant hurdle when considering an ethics hotline or anonymous reporting software. With Elker, we’re with you all the way.
- Full service: We handle the whole process: setup, technical implementation, advice and training
- Points of contact: For organisations unequipped to address incidents, our legally trained experts are available to assist
- Guidelines and training: Our comprehensive guides equip your staff to use the software and handle incidents with compassion and expertise
- Customer success: Each client is paired with a customer success representative, guaranteeing a smooth onboarding process
Data protection and platform security
Our anonymous reporting platform is built on trust. We go beyond industry standards to ensure data is encrypted everywhere and protected using the highest possible security protocols.
- Security and privacy: Our security policies are written consistently with an ISO27001 typology
- No tracking, no advertising: We don’t employ third-party tracking services or advertising, prioritising user privacy
- Data location: We store your data in the national jurisdiction of your business, aligning with local data privacy regulations
- 3rd party security testing: We regularly engage a third party to evaluate and enhance our security measures.
Create a speak-up culture and tackle sexual harassment in the workplace
From December 2023, Australian businesses must comply with new Sex Discrimination Act guidelines. These guidelines outline our positive duty obligations to actively prevent sexual harassment and discrimination in the workplace. There are many sound business reasons to build a safe, ethical and compliant workplace.
Elker provides resources to update businesses on the Respect At Work Bill and other pertinent legislative changes.
Fraud prevention and accountability
A recent survey by PWC highlighted the effectiveness of internal fraud prevention mechanisms in combatting financial crime. The positive shift underscores how a robust whistleblowing system can play a vital role in maintaining a company’s integrity and financial health.
Elker provides businesses with comprehensive whistleblowing software, including employee surveys and analytics, to audit your company culture and gaps in compliance. Early detection is vital. With Elker, you can prevent employee misconduct from becoming a major public incident.
Who uses Elker?
Elker has become the trusted solution for Australian universities, businesses and peak bodies to transform their workplaces into safe and compliant organisations.
Universities
Address campus safety and misconduct with holistic reporting and case management. Join the University of Melbourne and make much-needed changes in your campus today.
Government departments
Manage public interest disclosures safely and effectively. Promote the integrity of the public sector and eliminate corruption and misconduct.
Businesses
Eliminate sexual harassment, bullying, discrimination and fraud in the workplace with anonymous reporting, cultural audits and case management. Join Solotel, AirRoad and Allens in creating a safe work environment for employees and taking steps toward compliance and prevention.
Peak bodies
Improve community relations and centralise feedback from your members. Join Women’s Community Shelter, Victoria Legal Services Board + Commissioner and YoungCare in fostering safe and transparent representative organisations.
Blog
The latest insights on anonymous reporting, Respect at Work compliance, fostering a speak-up culture, and employee misconduct in the workplace.
Frequently asked questions
Interested to find out more?
Get a walk-through of our anonymous reporting platform. See how Elker can help with compliance and build a culture of trust in your organisation. Friendly, no obligations, no pushy sales strategies.